Third-party risk management (TPRM) has grown in prominence as organizations increase their reliance on external parties, from cloud providers to credit card processors. As more enterprises invest in this critical business function, certain best practices are becoming key to a successful TPRM program.
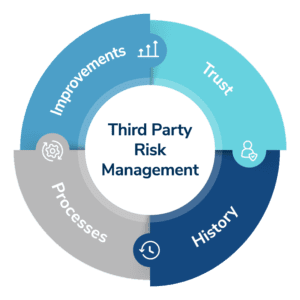
The authors of this article, a consultant and third-party risk manager for the international retailer AutoZone and an executive at investigations firm Kroll, joined forces to examine how to build or enhance a TPRM program, with specific input from the enterprise and consulting perspective. Through this analysis, the authors developed the trust, history, improvements and process (THIP) model, recognizing the vital role of emotional intelligence or emotional quotient (EQ), to define each as key components of third-party risk program enhancement or development.
Trust: The Value of Building from Experience
Consultants are used to working with many organizations, all facing different challenges. A constant for all remains the need to build trust. What has led some to become unable to do this on their own?
As an “outsider,” one of the key benefits that a third-party consultant can give to their clients is a different perspective on where they have been and where they are going. They can also help organizations build bridges internally.
It is not just about giving an opinion; it is much more than that. It is about listening to their stories, helping them find their path and guiding them along it.
 Nurturing Buy-In from the Enterprise
Nurturing Buy-In from the Enterprise
At the enterprise level, building a TPRM program calls for a unique set of skills, none more important than relationship-building. The first order of business is to determine the stakeholders most integral to the program’s strategic success. They will serve as the program’s brand ambassadors and are largely the sole determinant for ensuring the program’s success. It’s the job of the program leader to teach these stakeholders how to evangelize for the program so that, as the program is launched, it’s not the first time other stakeholders have heard about it.
How do you get the stakeholders to care about your program? You find a way to deliver value directly to their process or functional area. You achieve that by learning about their pain points and then help address them.
History: It Matters
A key first step is to identify what the real drivers are. What does the program need to do?
Organizations continue to face both internal and external challenges with this issue. First among them is that there are often some negative emotions associated with third-party risk. The source of this is usually one of the two areas:
- The organization doesn’t have a program and needs one; or
- The organization does have a program but needs a better one.
If the organization doesn’t have one, the driver is often an outside stimulus, possibly an audit, but sometimes it is the board or leadership reacting to a compliance requirement.
Being “forced” to start or expand a program is often considered a necessary evil by certain business units, especially those for whom security is just a formality.
Identifying these issues is the first step to understanding the actual pain point. We have learned that people may say that they have one challenge — doing more assessments, for example — but the stories they share may paint a different picture.
Learning about and from these experiences is just one reason why it is important to meet and talk with as many people in an organization as possible.
It’s common to encounter silos based on negative history when creating a new addition to an enterprise, especially one that will affect every single functional area. This can have a detrimental effect when attempting to ensure a new program is accepted. The best way to erase a negative history is to paint the promise of a better future. And that promise begins with building a relationship grounded in trust.
Building from individual and team experiences is vital for nurturing trust. A narrative of this kind always has a moral. Listen for the point each person is trying to share.
In third-party risk, there are different types of narratives, but they generally fall into one of the two categories:
- The business unit involved was negatively affected because the assessment process was too long, arduous or incomplete.
- The security/compliance unit has been let down by lax assessments, missed assessments or struggles to achieve buy-in.
These experiences, while they may seem different, represent a common theme: the breakdown of trust. So, one of the first goals should be to re-establish trust. First, so that people take recommendations seriously and second, to empower appropriate groups to implement the recommendations.
After listening to the stories and the “moral,” the next step is to start mapping relatively easy wins. Action is the best way to build trust but not in relation to the complicated challenges initially. For example, there may be an overarching problem, perhaps the need for a comprehensive inherent risk framework for all third parties, but it shouldn’t be the focus at this stage.
It is more effective to ask the business units to organize their vendors into tiers or categories of readily apparent risk instead of pushing for a much more extensive review.
In this early stage, the ability to chart a “win-win” for all sides is paramount. The first tasks may seem minor, but they are the stepping stones that can help lead an organization to where it needs to be.
Trust is built by following through on promises. How might we expedite it? By making quick-win promises and delivering quick-win results. Once trust is established, it is possible to begin introducing discrete stages of enterprise strategy. This helps in generating frequent successes and sustained team and stakeholder morale while moving toward identifying procedural gaps and removing culturally embedded obstacles.
Improvements: Invention or Innovation?
Understanding third-party management in general helps identify those quick wins to build trust, but it also enables the organization to understand the bigger picture and head in the right direction. Problem-solving requires two approaches:
- Invention: Invention is where the organization will look to build new programs. If there wasn’t something before, this is an obvious first step. But even if there was something before, if the trust in it was broken, starting anew may be the right choice. While invention is challenging, it is the best way to build trust in many cases.
- Innovation: If there is sufficient trust in the processes that exist or the organization can salvage them, innovation is the better option. Innovation is when existing programs are looked at critically and optimized to meet all involved needs more effectively.
The key to making either of these paths successful is being prepared to listen, to identify both the short-term problems and the structural challenges and to ensure that the third-party cyber risk management process aligns with the third-party management process.
Process: Make It Count
Understanding the potential quick wins starts with understanding processes. This involves learning as much about the current process of third-party management as possible. Key to this is analyzing how the organization:
- Views third parties: Are the third parties critical partners for the business units, or is it more transactional? This attitude will significantly impact how the client views the requirements they establish for their third parties.
- Acquires third parties: What is the process of adding new third parties into their business process? Is it usually a formal RFP process with many opportunities to check security controls? Or is it loose and flexible, with business units having wide latitude to add or change third-party roles? The second approach will make it easier to add in new assessment processes, while the first will require a focus on inherent risks.
- Works with third parties: How do the business units work with them? Are they closely monitoring their productivity and actions? Or is it more hands-off? Being closely aligned makes it possible to add a new assessment process, but it also makes the business units more sensitive to impacts on their work.
The worst mistake is to assume that existing processes aren’t being used; those are the types of assumptions that can lead to new silos.
EQ Equals Better Third-Party Risk Programs
This article was written to address the EQ gap associated with building or improving a TPRM program, or as they’re more commonly known, the soft skills or people skills aspect of the equation.
The THIP model was developed with the aim of closing the EQ gap and cultivating more mature, emotionally intelligent third-party risk programs. Success in this sector is dependent upon multiple factors, none more important than emotional intelligence; EQ in this context means understanding the interrelationships between people and processes and the vital impact — positive or negative — that these can have on third-party programs.
As the THIP model harnesses and nurtures key human qualities, it should serve as a more robust and sustainable basis for TPRM programs. For third-party risk managers either starting or building out a new program, we highly encourage they use the THIP model as a framework for planning actions and measuring success.