Evan Francen, CEO of FRSecure and Security Studio, makes the case for adopting a third-party information security risk management (TPISRM) program. He outlines how to get started and explains why the common excuses for ignoring the risks don’t hold water.
Third-party information security risk management (TPISRM*) is more critical today than it’s ever been. There is little doubt amongst information security experts that TPISRM is essential to the success (or failure) of your information security efforts, but the confusion in the marketplace is making it difficult to tell truth from hype. Ignoring the risks won’t make them go away, so something must be done. We just need to make sure it’s the right “thing.”
The Case for TPISRM
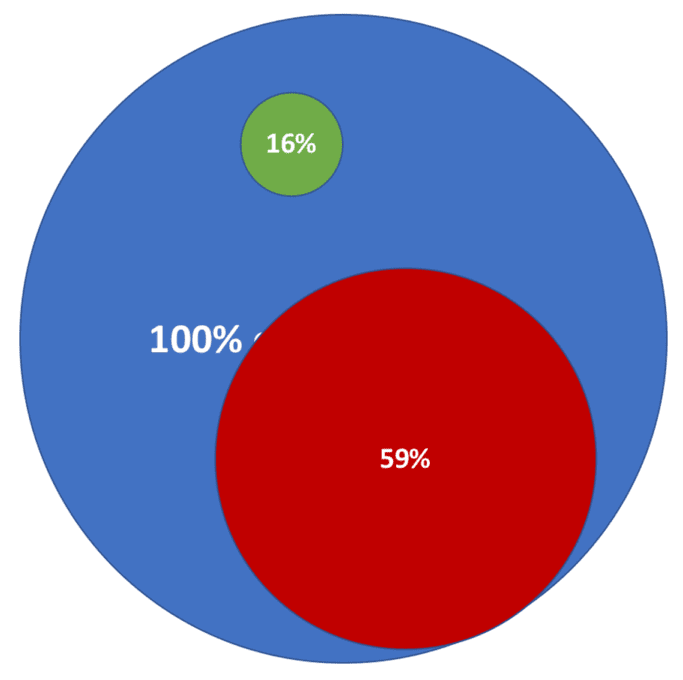
If the case for TPISRM isn’t obvious to you, you’re not alone. Only 16 percent of the 1,000 Chief Information Security Officers (CISOs) surveyed in a recent study claim they can effectively mitigate third-party risks, while 59 percent of these same CISOs claim their organizations have experienced a third-party data breach.[1]
 Third parties are implicated in up to 63 percent of all data breaches[2] and regulators are increasingly scrutinizing how organizations handle third-party risks. Your organization can spend millions of dollars on a secure infrastructure, best-in-class training and awareness solutions and the most skilled professionals, but if you neglect to account for third-party risks, some or all of your investment is a waste.
Third parties are implicated in up to 63 percent of all data breaches[2] and regulators are increasingly scrutinizing how organizations handle third-party risks. Your organization can spend millions of dollars on a secure infrastructure, best-in-class training and awareness solutions and the most skilled professionals, but if you neglect to account for third-party risks, some or all of your investment is a waste.
Please let these numbers sink in for a moment. Logically, how do we deny the need for sound and cost-effective TPISRM when we know that it will decrease the likelihood and impact of a data breach? Logic says one thing, yet 57 percent of organizations don’t even have an inventory of the third parties they share sensitive information with.
Common Excuses For Not Establishing a TPISRM Program
We have other, higher-priority initiatives right now.
Most of us have dozens (maybe hundreds) of projects and tasks to complete at any given time. It’s very difficult to discount the statistics about third-party incidents and breaches and justify that it’s not a high priority for you. Difficult, but not impossible. If you can justify that other initiatives are higher priority, you should document this logic for when the inevitable happens. The numbers indicate that it’s only a matter of time before a mistake made by a third-party or negligence on their part will cause you harm.
We don’t have TPISRM in our budget.
You don’t need much, if any, money to get started with TPISRM. Start with a compiling a third-party inventory, which won’t cost you anything. If you’re creative, it won’t even cost you much time. Send an email or go talk to your finance team. Ask them to provide you with a list of all third parties your organization is paying through invoices, corporate credit card payments or employee reimbursements. Now you’ve got a start, and this could be used to justify a budget. Another important note about budget: There are several quality products on the market that can be used for less than $200 per month.
We don’t employ enough third parties for it to matter that much.
Every organization has at least one third-party relationship, and all it takes is one. Fewer third parties just means less work, not no work.
We don’t have anything that anyone would want. We’re not a target.
This fallacy has been disproven thousands of times. Don’t make the mistake of thinking you know the motivations of attackers. Some attack for money, some for notoriety, some for power, some for revenge and some just want to cause chaos. Everyone has something someone wants.
There are few valid excuses for not establishing a TPISRM program. Logically, it doesn’t make sense to not account for risks when we know that most data breaches come through third-party relationships and that other people inherently treat other people’s things (data) with less care than they do their own. The market understands this, your competitors are waking up to this and compliance officials (agencies, regulators, auditors and investigators) are using more scrutiny than ever.
Failing to establish your own TPISRM program will come with consequences – some of which may be severe.
Assumed Breach
No matter what you do, you cannot prevent a third-party breach in all cases. The goal isn’t to eliminate risk. The goal is to manage risk. A breach will happen. This is the reality or risk, so play it out.
Assumed breach is a thought or logic model. Informally (which is fine for now), it works by putting yourself mentally into a breach scenario. The best way to go through the assumed breach scenario is to ask yourself a series of questions, anticipate outcomes and predict next steps. Here’s a sample effective assumed breach scenario for TPISRM:
- You find out you’ve been compromised by an attacker through one of your third-party providers. What do you do?
- You’ve been sued in response to the breach. What questions will opposing counsel ask you?
DISCLAIMER: Although I’ve worked with dozens of lawyers on data breaches, I am not a lawyer. None of the information in this article should be considered qualified legal advice.
This is where your answers determine your defensibility. A civil case hinges on a preponderance of the evidence, and what’s often in question is whether or not you’re negligent. Negligence is a failure to behave with the level of care that someone of ordinary prudence would have exercised under the same circumstances.[3] Your answers matter. Defensible answers tip the scale in your favor, poor answers tip the scale the other way. Here are some reasonable questions you could expect from opposing counsel:
- Did you know that third parties cause or are implicated in a majority of all data breaches?
- Did you know that data breaches caused by third parties are on the rise?
- Do you have a third-party information security risk management program?
- How many third parties does your company employ?
- Do you classify your vendors?
- How many high-risk/high-impact third parties does your company employ?
- Do you conduct risk assessments on all high-impact third-party relationships?
- Do your risk assessments account for the administrative, physical and technical aspects of information security?
- Are all high-impact third-party relationships assessed the same way?
- Have you established what an acceptable level of risk is versus what is unacceptable?
A reasonable and objective assumed breach scenario would lead you to questions like the 10 outlined above. To ensure your defensibility, you should have good answers to each of the questions with as much certainty as possible. You would think that anything other than a definitively defensible answer would probably lead opposing counsel to inquire further and cause more doubt in the minds of the judge or jury.
Defensibility is very important for executive management and boards of directors. Defensibility might be the explanation for why 15 percent more boards were involved in TPISRM in 2017 versus 20161, a positive trend.
Let Logic Be Your Guide
Avoid the hype and use logic to guide your TPISRM decisions. By now, you should be convinced that you should (or must) engage in TPISRM. The assumed breach approach will help you determine what it takes to put you and your organization in a defensible position. We learned that defensibility in TPISRM requires at least the following:
- That you engage in TPISRM. More formality in your approach is better.
- A third-party inventory. You can’t defend against what you don’t know you have. You have to know who your vendors are.
- A third-party classification scheme. Classification shows you’ve at least considered the risks your third parties pose to you. Not all third parties are used the same way.
- A third-party assessment methodology. Classification drives the type and depth of the risk assessment. It only makes sense that you would scrutinize third parties who handle your most sensitive information more than you would scrutinize a third party that never handles anything.
- Thresholds and remediation requirements. Your organization can only tolerate so much risk, so define how much risk that is. Remediate everything below the threshold or avoid the risk altogether.
What else can you think of that makes an organization defensible with respect to TPISRM?
*My apologies for another acronym, I realize we have enough in our industry already. I use it in the article because it saves me a lot of writing and it saves you some reading.
[1] https://www.businesswire.com/news/home/20181115005665/en/Opus-Ponemon-Institute-Announce-Results-2018-Third-Party
[2] http://www.marketwired.com/press-release/soha-systems-survey-reveals-only-two-percent-it-experts-consider-third-party-secure-2125559.htm
[3] https://www.law.cornell.edu/wex/negligence
Sources
- http://www.marketwired.com/press-release/soha-systems-survey-reveals-only-two-percent-it-experts-consider-third-party-secure-2125559.htm
- https://www.opus.com/ponemon-2017/
- https://www.law.cornell.edu/wex/negligence
- https://www.businesswire.com/news/home/20181115005665/en/Opus-Ponemon-Institute-Announce-Results-2018-Third-Party



 Evan Francen is an information security expert with more than 25 years of "practical" information security experience. He has an ambitious mission: fix the broken industry.
Evan is the CEO of
Evan Francen is an information security expert with more than 25 years of "practical" information security experience. He has an ambitious mission: fix the broken industry.
Evan is the CEO of