In many spheres, PCI DSS is like the law of gravity: It affects just about everything. PCI DSS 4.0, the first major update since 2013, is right around the corner. If your business so much as smells cardholder data, this article is for you.
Payment Card Industry Data Security Standard (PCI DSS) has become the leading set of security standards for maintaining a secure environment for all companies. Any organization that accepts credit, debit or prepaid cards under the American Express, Discover, MasterCard, Visa and JCB brands must maintain PCI DSS compliance. The latest version of the standard, PCI DSS 4.0, will be released in Q1 of 2022, prompting companies to start preparing for what’s ahead. This article will discuss the changes in the new version of PCI DSS 4.0, including the key priorities and goals, three steps to adhering to PCI DSS 4.0 and tips for successfully maintaining ongoing compliance.
https://twitter.com/annnwallace/status/1174127471127478272
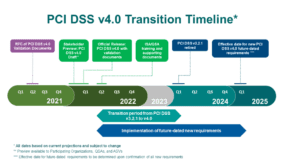
The long-awaited PCI DSS version 4.0 is the first major change to the standard since the end of 2013. While PCI DSS 4.0 is expected to be released in Q1 of 2022, the current PCI 3.2.1 will not be retired until Q1 of 2024. This gives companies plenty of time to finish off any existing reports on compliance (ROCs) while also providing additional time to become compliant with the new 4.0 standards.
The goals of PCI DSS 4.0 include a focus on persistent, end-to-end personal data protection for processing payments in modern data environments. According to the PCI Security Standards Council, “PCI DSS is being updated to address … stakeholder feedback and to support a range of environments, technologies and methodologies for achieving security.”
Experts agree that version 4.0 is expected to require far more stringent security on the part of credit card processing organizations while allowing greater discretion and freedom as to how implementations for meeting these stricter expectations can be customized. Version 4.0 is also positioned to more forcefully mitigate against rampant data breaches that have been consistently compromising cardholder private and personal data.
Key Differences in PCI DSS 4.0
PCI DSS 4.0 is expected to differ from the current PCI DSS version 3.2.1 in a few key ways. One of the biggest changes is that PCI DSS is giving more leeway regarding “how” an organization can become compliant.
PCI DSS 3.2.1 and its predecessors included not only a series of objectives (e.g., protect cardholder data), but also very specific requirements that dictate exactly how companies must achieve those goals. In other words, the standard is extremely prescriptive. Should a business be unable to follow these prescriptive steps to compliance, they must implement a compensating control. This can often be an extremely time-consuming and costly procedure that requires an organization to go well above and beyond the intent of the primary control itself.
Here are the three main differences in version 4.0:
Customization
PCI-DSS 4.0 does keep the existing prescriptive method for compliance, should an organization want to continue cookie-cutter security. However, 4.0 is replacing compensating controls with an alternate option: customized implementation. Customized implementation takes into consideration the original intent of the objective and allows organizations to design their own security controls to meet it. Once an organization determines the security control for a system, network or other object, it must provide full documentation to enable their PCI Qualified Security Auditor (QSA) to make a final decision on the effectiveness of a control. Should the QSA not accept the control or the documentation, the organizations may then be asked to enhance it, alter it or potentially go back to the prescriptive control requirement.
Cloud and Serverless Computing
Another area that’s expected to change will be around the use of cloud and serverless computing. The core controls of the current version 3.2.1 were not designed for modern IT environments that often leverage multi-cloud, on-premises and vendor networks. Version 4.0 will introduce an updated set of requirements and approaches to securing cloud and serverless workloads.
Control Requirements
Organizations can also expect new control requirements, such as an expansion of cardholder data encryption over any transmission, including within trusted networks. There is also likely to be a control requirement update regarding multifactor authentication and logins. With the tremendous advancement in this technology, the PCI Security Standards Council Site will possibly want to see those in use.
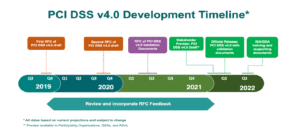
The Importance of These Changes
The 12 foundational requirements and list of controls included in PCI DSS 3.2.1 will still be a part of 4.0, but the addition of the customized implementation option introduces new flexibility for companies to use a broader range of methods and technologies to achieve each PCI objective. And, ultimately, organizations might find a more cost-effective or simpler way to comply.
Another potential perk of the ability to now build in “unique” controls is added confidence against the effectiveness of attacks designed to outmaneuver the more prescriptive approach published by PCI. In addition to this, organizations that take their data security seriously will be more open to creating various unique ways and methods to product their card data environments (CDEs).
Three Steps to Adhering to PCI DSS
Complying with PCI DSS can be a complicated journey, and leveraging the assistance of an external consultant or third-party auditor is a wise move. Whether you have the internal resources to run your adherence campaign or leverage outside expertise, the road to PCI DSS compliance can be boiled down to three steps:
Assess: Perform an audit to identify the cardholder data the organization is responsible for, inventory IT assets and business processes involved in payment card processing, and analyze for vulnerabilities.
Remediate: Fix any vulnerabilities uncovered in the assessment stage. If the organization is storing unnecessary cardholder data, take steps to properly dispose of it. For businesses that need to retain cardholder data, consider leveraging an external qualified body for storage or investigate proper remediation techniques, such as redaction and/or encryption.
Report: Assemble and submit any applicable required remediation records and compliance reports.
Ensuring PCI DSS 4.0 Compliance
Once a company has earned PCI DSS compliance validation, it needs to ensure the proper maintenance to stay compliant. Maintaining compliance starts by putting checkpoints into the governance, risk and compliance or workflow system. Companies should start by asking the various IT teams every 30 days or every quarter for particular PCI DSS requirements. These checkpoints could be as simple as an automated ServiceNow or JIRA ticket that informs the network engineer or DevOps person that they need to provide specific evidence of an access review, network drawing or other piece of data. Implementing this strategy can help ensure PCI DSS compliance never becomes a “project,” and it can save a company millions of dollars year over year.
Now, keeping all of this in mind, it’s also important for a company to know what its CDE is. After all, scoping the PCI DSS ROC is roughly 80 percent of the battle. This is an exercise where a company’s compliance team will sit down with the various business units and start to understand any system or service that touches, processes, stores or passes any PCI data. This is another critical way to ensure ongoing compliance success.
Preparing for PCI DSS starts with being compliant with the most current version, 3.2.1, then planning for the changes necessary in version 4.0 to adapt to new requirements and security testing. By following the three basic steps outlined and keeping in mind the strategies mentioned above for ongoing compliance, companies will be well on their way to having a seamless transition to PCI DSS 4.0 and also to maintaining compliance in the years to come.



 Chris Pin is the Vice President of Security and Privacy at
Chris Pin is the Vice President of Security and Privacy at