An IT-centric network perimeter security model is increasingly insufficient to protect your organization from cyberattacks. Onclave Networks’ Scott Martin advocates a “zero trust” approach to security as a means of reinforcing defenses.
Sponsored
The rise in cyberattacks and ransomware has awakened business leaders all over the world to a new reality: The threats to network and data security have grown beyond what many traditional security solutions can defend against.
Compliance regulations are continuously changing, from HIPAA to PCI to GDPR. This puts businesses at risk of missing important regulatory obligations, exposing them to increased responsibility. Fines, security breaches and negative operational effects can all be avoided with a comprehensive, integrated strategy to compliance adherence, which includes vendor management.
In the last several months, we have seen supply chain attacks and breaches within our critical infrastructure. Everything from our food, energy and water to hospitals, first responders and both large enterprises and small businesses have experienced firsthand how sophisticated and well-financed criminal organizations, as well as nation states, can wreak havoc by stealing sensitive data and disrupting operations.
The rise in cyberattacks is not just a blip on the radar or some post-COVID-19 trend that will ease soon. Cyberattacks are rising.
Digital modernization and the convergence of information technology (IT) and operational technology (OT) have greatly expanded the surface area of our networks and made them more vulnerable to attacks.
Business leaders need to recognize the rapid growth in OT – which includes the internet of things (IoT), industrial internet of things (IIoT) and industrial control system (ICS) – and understand that these devices and systems are on a converged IT/OT network using the same wires to transmit data. However, OT is not protected by traditional IT security solutions.
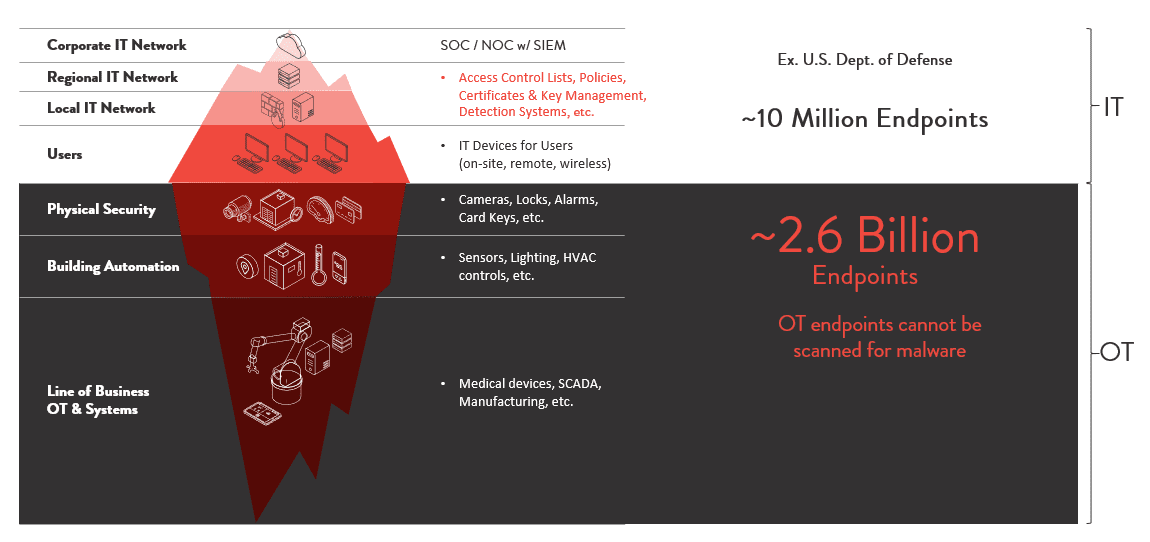
The typical IT-centric approach and tools currently used to protect communications fail to address known vulnerabilities inherent in the wide array of architectures, software and equipment. This is because they are designed and built primarily for an “open” communications framework.
A standard IT way of securing an enterprise is to “trust, but verify.” In many cases that means that once data or a user has gotten past a security layer, the remaining network is open. However, given the number of vulnerable OT endpoints that are unprotected by IT security, cyberattackers have access to more endpoints they can exploit. Once inside a network, they can roam undetected for several months to a year, leaving malware and stealing data. And, nowadays, with the evolution of cloud computing, networks and IT environments, the network perimeter security model is no longer sufficient.
Fortunately, there are ways business leaders can secure the edges and reduce the rapidly expanding attack surface created by the IT/OT convergence. One of the most compelling is the adoption of Zero Trust principles for cybersecurity.
Adoption of Zero Trust Principles for Cybersecurity Is on the Rise
Gartner estimates 60 percent of businesses will shift to zero trust networks by 2023. A separate global study showed that 42 percent had plans to adopt a zero trust strategy and are in the early phases of implementation.
The U.S. federal government also has been moving toward zero trust as new directives and guidelines have emerged from the U.S. National Security Agency (NSA), the Biden Administration executive order 14028 and National Institute of Standards Technology (NIST) SP 800-207 Cybersecurity Framework.
But what does this adoption of zero trust mean to you and your business? Why implement a zero trust network security architecture?
To answer “why,” it is helpful to understand “what” zero trust is all about.
In short, zero trust is not a product, software or a specific network, but a strategic approach to security. A zero trust network no longer assumes trust should be given once network access has been achieved, nor at a single entry point. Instead, to ensure security, any user, device or system must be verified at each network access point. This essentially changes your cybersecurity approach from “trust, but verify” to “never trust, always verify.”
Benefits of Adopting a Zero Trust Network
At Onclave Networks, we highly recommend zero trust as an important framework for your network security. One of the critical areas where businesses can enhance their security is by applying those guidelines to their network. As noted above, there have been fundamental changes in network traffic patterns that have made most existing network security models ineffective. Onclave is uniquely positioned to continuously reassess trust to ensure the most secure communications.
The Onclave TrustedPlatform™ was designed with Facilities Related Controls System (FRCS), Physical Security, SCADA, IoT/IIoT devices and OT systems in mind. Onclave’s solution is based on a NIST-aligned, integrated zero trust framework, enabling Secure Access Service Edge (SASE) capabilities, such as cloud management and the ability to bring the security stack to the edge.
Onclave’s platform creates secure enclaves by cryptographically separating OT/IoT from the IT network – eliminating attack surfaces and protecting enterprise data communications and operations. The single, integrated communications platform provides detection, isolation and containment capabilities through continuous monitoring of all endpoint activities and, importantly, it requires no changes to an organization’s existing infrastructure. Combined, this solution reduces the organization’s costs from cyberattacks, overhead and compliance risks.
 Based in the Washington, D.C., area, Onclave Networks, Inc. is a global cybersecurity leader that specializes in securing operational technology (OT/IoT) through private networks. Onclave provides the first, true Zero Trust secure communications platform that protects both legacy and new operational technologies from cyberattacks and other types of unauthorized access. Onclave makes trusted secure communications a standard for all by providing the fastest path to a more secure, simplified, and cost-effective alternative to today’s solutions.
Based in the Washington, D.C., area, Onclave Networks, Inc. is a global cybersecurity leader that specializes in securing operational technology (OT/IoT) through private networks. Onclave provides the first, true Zero Trust secure communications platform that protects both legacy and new operational technologies from cyberattacks and other types of unauthorized access. Onclave makes trusted secure communications a standard for all by providing the fastest path to a more secure, simplified, and cost-effective alternative to today’s solutions.
For more information, visit onclavenetworks.com, download our Zero Trust whitepaper or Contact Us for more details.



 Scott Martin is Chief Marketing Officer at
Scott Martin is Chief Marketing Officer at 






