As part of its ongoing commitment to cyber threat research, Kroll’s threat intelligence team looked at hundreds of real-life cyber incidents to determine how intrusions occur. Alan Brill, senior managing director of cyber risk at Kroll, explains what they’re seeing and what should be of concern to every compliance officer.
In short, Kroll’s team has seen a staggering increase in two specific sets of cyber-attacks: those exploiting known common vulnerabilities and exposures (CVEs) and those exploiting previously unknown “zero-day” vulnerabilities. Brill shares more background, plus a few ideas on how organizations should respond.
‘Software Exploits Abound’
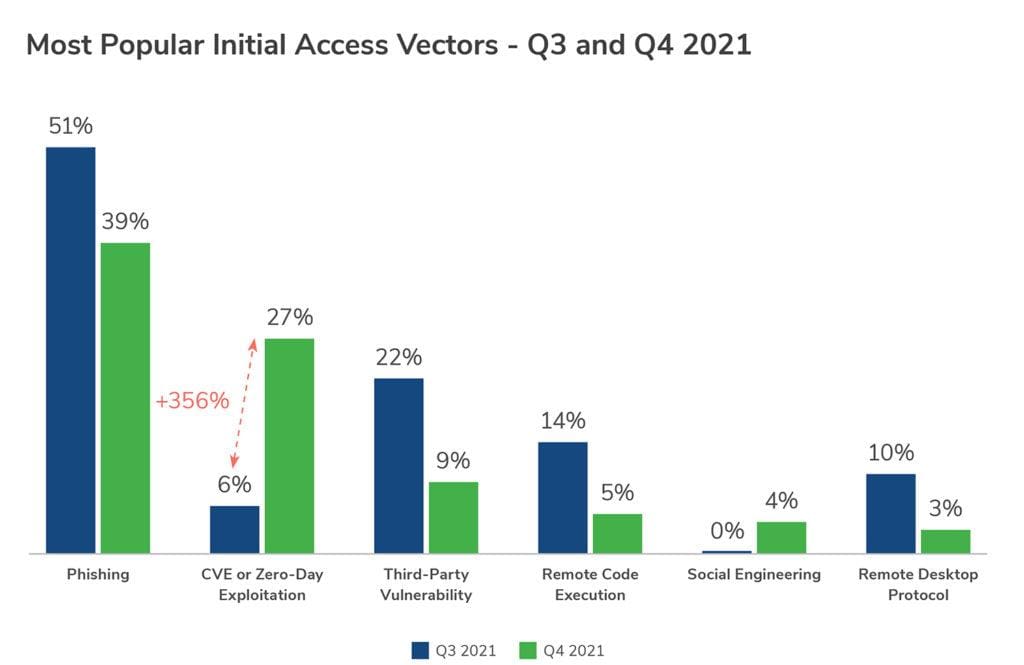
CVEs, typically targeted by hackers, plus zero-day vulnerabilities, which form the basis for assaults from bad actors including nation-states, hacker groups or individual criminals, are on the rise. Kroll’s report Q4 Threat Landscape: Software Exploits Abound shows that relative to the third quarter of 2021, in the fourth quarter of last year, the incidence of these two threats rose a remarkable 356 percent.
 This extraordinary growth of CVE/zero-day attacks is something that should be addressed by every company. CVEs, or security issues that have been identified in existing software, can be used to plant malware or ransomware or to target valuable sensitive data for theft.
This extraordinary growth of CVE/zero-day attacks is something that should be addressed by every company. CVEs, or security issues that have been identified in existing software, can be used to plant malware or ransomware or to target valuable sensitive data for theft.
In contrast, zero-day attacks are unique and previously unknown. However, once an attack is recognized, industry teams respond. Typically within a matter of hours for significant attacks, researchers analyze the intrusions and where possible, publish defensive steps along with ways to identify attacks through specific “indicators of compromise” (IOCs). At that point, the zero-day attack becomes a CVE.
Assessing Risks
Overall, phishing attacks remain the most frequent infection vector, accounting for 39 percent of all suspected initial access methods. But the extraordinary growth in CVE/zero-day exploitation represents an ominously rising danger.
Predicting any organization’s vulnerability to a particular CVE or zero-day assault is extremely difficult, as there may be no way for the organization to know if it is running software containing the vulnerability. Many CVEs are part of generic libraries or common routines that are embedded in software already in use. And because the concept of “software bills-of-materials” is historically unpopular (software manufacturers consider their code to be a trade secret), it becomes virtually impossible to fully understand your embedded code risk. That is, a company will not know that it is running vulnerable software until early breaches occur and are investigated.
For example, the recent Log4j vulnerability involved a component found in several versions of Apache, the most commonly used web server software. The problem involved open-source code built and maintained by a software foundation and eventually incorporated into Apache. But because it was part of those builds of Apache, thousands of companies were vulnerable but had no practical way of knowing their risk level.
For compliance professionals, this highlights the importance of having a robust process in place to ensure that all of the software used, whether written in-house or acquired from outside vendors, is maintained with critical updates implemented immediately unless there is a specific reason not to do so. In those cases, there must be either a security workaround until the software can be patched or a recognition on the part of management that it is accepting an increased level of risk.
Too often we see intrusion victims who did not apply patches fearing doing so might disrupt how their systems worked. In some cases, we found attacks targeting problems where effective patches had been available for months or even years but were not installed. There also have been cases where a particular end-user’s device wasn’t patched. Perhaps they were on vacation when the patch was released and the attackers used that machine to gain entry to the entire network.
Responding to Rising Risks
While there is no perfect solution to the CVE and zero-day challenges facing IT departments, given the meteoric rise in successful attacks, it should be clear that ignoring the problem — failing to implement an organized solution — is unacceptable. If they haven’t done so recently, compliance teams need to undertake a CVE/zero-day readiness assessment. Ask:
- Are there written standards, policies and practices that define how your organization monitors and identifies CVE/zero-day issues?
- Is there a system in place to track the installation of patches as they are released?
- Is there a good source of threat intelligence available to the organization, or do they wait for an incident to occur or for a vendor to tell them that they have a vulnerability?
- Does the company have sound procedures in place for remediation?
- Is there recordkeeping in place to provide assurance that previously identified problems have been appropriately addressed?
In general, ask how the IT unit recognizes cyber risks and how they manage the remediation effort. Note that due to open-source code and libraries having been in use for many years, software developers may not be sure exactly what is embedded in their systems. Moreover, recognize that your vulnerability may be expanding: think about any software embedded in increasingly ubiquitous Internet of Things (IoT) devices.
Bringing Compliance Skills to the Cybersecurity Table
Organizations are recognizing that continuously monitoring their networks’ cyber-health — maintaining a 24/7 security operations center or contracting to have specialist organizations provide them with continuous monitoring, analysis and notification — is quickly becoming the gold standard in cyber security. Taking the time to think through a solution that is right for your organization’s particular needs is vital. Here we are seeing a range of useful and interesting responses to this cyber security issue and related challenges.
Step one, in handling thousands of actual cyber intrusions each year, we consistently observe that there is a close correlation between overall cyber security readiness and the engagement of compliance professionals. For this reason alone, a growing number of organizations have appointed a chief information security officer (CISO).
While a step in the right direction, a CISO can be costly, and for a small- to-medium-sized network, unrealistic. Accordingly, many companies are embracing the concept of a “virtual CISO.” A “V-CISO” enables multiple organizations to share the cost. The V-CISO provides services to the group of companies, giving them capabilities affordable only to larger firms. The V-CISO helps with both incident prevention, identification, response and recovery.
In parallel, companies need to achieve continuous monitoring. While it is fair to say that most companies can’t afford to run a cyber security operations center around the clock staffed by experienced specialists, there is an effective alternative. Monitoring specialists can place sensor software in an organization’s network to watch for known risks and anomalous activity, allowing them to see early warnings of potential problems. Moreover, the provider is able to leverage knowledge gained from monitoring thousands of endpoint systems.
The V-CISO model enables specialists to leverage knowledge gained by monitoring thousands of endpoint systems. As such, they are well-placed to identify not only CVE and zero-day issues but a wide array of risk vectors. In this way an organization can receive a level of service that they could not individually afford, improving their cyber security at a more reasonable cost.



 Alan Brill is a senior managing director with Kroll's
Alan Brill is a senior managing director with Kroll's